
Introduction
In modern enterprise environments, DevOps practices and hybrid cloud architectures have become tightly linked. Organizations rely on hybrid cloud setups to balance flexibility, cost, and performance while adopting DevOps methodologies to accelerate software delivery and innovation. However, this combination brings unique security challenges because data, code, and infrastructure are distributed across on-premises environments, private clouds, and public clouds.
Securing a hybrid cloud DevOps environment requires a multi-layered approach, covering infrastructure, tools, processes, and access controls. Below, we will explore key strategies, features, and best practices to enhance security in hybrid cloud DevOps setups, ensuring seamless development, delivery, and operations without compromising data integrity or compliance.
1. Identity and Access Management (IAM) Across Environments
In a hybrid cloud DevOps environment, teams, tools, and systems operate across multiple cloud providers and on-premises infrastructure, making identity and access management (IAM) critical for security. Developers, CI/CD pipelines, automated processes, and services all require appropriate permissions, but excessive access can lead to breaches.
Key Features and Best Practices:
- Centralized Identity Management: Implement a single identity provider (IdP) for all environments (on-prem, private cloud, public cloud).
- Role-Based Access Control (RBAC): Assign granular roles and permissions to users, tools, and processes.
- Just-in-Time (JIT) Access: Grant temporary access when needed rather than permanent credentials.
- Multi-Factor Authentication (MFA): Enforce MFA for all privileged access.
- Audit and Logging: Continuously monitor authentication events and access patterns across hybrid environments.
2. Secure CI/CD Pipelines Across Hybrid Cloud
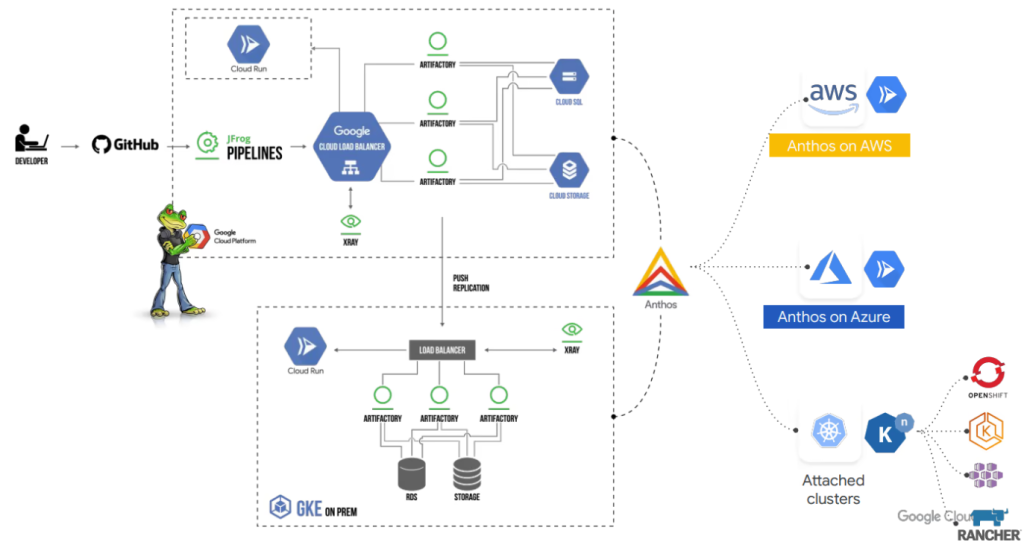
In DevOps, continuous integration and continuous delivery (CI/CD) pipelines form the backbone of automated deployments. In a hybrid cloud, these pipelines span on-prem build systems, cloud-based repositories, and deployment environments across multiple clouds, increasing the attack surface.
Key Features and Best Practices:
- Code Repository Security: Protect Git repositories with branch protection rules, encryption, and access controls.
- Pipeline Credential Management: Use secrets management solutions to store API keys, passwords, and tokens securely.
- Artifact Integrity: Implement checksum verification and signed artifacts to ensure no tampering.
- Segregated Environments: Separate development, testing, and production pipelines to reduce accidental exposure.
- Pipeline Audits: Continuously audit pipeline activity for anomalies and unauthorized changes.
3. Hybrid Cloud Network Security and Segmentation
In a hybrid cloud DevOps environment, applications and services communicate across cloud and on-premises networks. Ensuring secure connectivity while minimizing attack surfaces is essential, especially when pipelines and infrastructure span multiple providers and datacenters.
Key Features and Best Practices:
- Zero Trust Network Access (ZTNA): Restrict network access based on device identity, user role, and real-time risk assessment.
- Network Segmentation: Separate DevOps environments into isolated network segments with controlled inter-segment communication.
- VPN and Direct Connect: Use encrypted tunnels or private connectivity options to connect on-premises and cloud environments.
- Traffic Encryption: Enforce TLS encryption for all data in transit between environments.
- Continuous Network Monitoring: Use intrusion detection systems (IDS) and network traffic analysis tools across the hybrid cloud.
4. Automated Security Testing and Shift-Left Security
The DevSecOps approach, which integrates security testing early in the DevOps lifecycle, is particularly important in hybrid cloud environments, where application components may deploy across diverse platforms. Embedding automated security checks into CI/CD pipelines enhances early threat detection and reduces vulnerabilities before production.
Key Features and Best Practices:
- Static Application Security Testing (SAST): Scan code for vulnerabilities during development.
- Dynamic Application Security Testing (DAST): Test running applications for security issues in staging environments.
- Infrastructure as Code (IaC) Scanning: Analyze IaC templates for misconfigurations and weak policies.
- Dependency Scanning: Identify vulnerable open-source components used in code.
- Security Policy Enforcement: Apply security gates that block deployments if critical vulnerabilities are found.
5. Hybrid Cloud Secrets and Configuration Management
Hybrid cloud DevOps environments rely heavily on API keys, credentials, and configuration files to connect applications, tools, and infrastructure. Poor management of these secrets can lead to data breaches, credential leaks, and unauthorized access.
Key Features and Best Practices:
- Centralized Secrets Management: Use dedicated secrets management platforms (like HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault) for all environments.
- Dynamic Secrets: Rotate credentials automatically after use to reduce long-term exposure.
- Least Privilege Secrets Access: Limit who and what processes can read secrets.
- Configuration Encryption: Encrypt configuration files and sensitive variables at rest and in transit.
- Secrets Audit: Monitor access logs and rotate secrets frequently to mitigate potential compromise.
6. Continuous Monitoring, Threat Detection, and Incident Response
Securing a hybrid cloud DevOps environment is not a one-time effort — continuous monitoring and real-time threat detection are essential to detect and respond to threats across cloud and on-premises infrastructure. The combination of DevOps speed and hybrid complexity means security incidents can spread quickly if not identified early.
Key Features and Best Practices:
- Unified Monitoring Platform: Implement a centralized monitoring solution that spans cloud and on-prem infrastructure.
- Log Aggregation: Collect logs from CI/CD pipelines, cloud services, containers, and on-prem servers into a central repository.
- Threat Intelligence Integration: Use up-to-date threat feeds to detect and block emerging attacks.
- Automated Incident Response: Define playbooks to trigger automated responses (e.g., isolate compromised resources) when threats are detected.
- Security Dashboards: Provide real-time visibility into security posture across the hybrid cloud DevOps landscape.
