Upgrade & Secure Your Future with DevOps, SRE, DevSecOps, MLOps!
We spend hours scrolling social media and waste money on things we forget, but won’t spend 30 minutes a day earning certifications that can change our lives.
Master in DevOps, SRE, DevSecOps & MLOps by DevOps School!
Learn from Guru Rajesh Kumar and double your salary in just one year.
Here’s a comprehensive post titled “Serverless Security: Best Practices for Protecting Your Apps” with expanded content for each section:
The Importance of Security in Serverless Applications
Serverless computing has revolutionized application development by abstracting infrastructure management and allowing developers to focus solely on writing code. However, with the convenience of serverless comes the responsibility of securing your applications. While the cloud provider handles many aspects of security, such as infrastructure, server provisioning, and scaling, the developer still needs to ensure that the application code, data, and communication remain secure.
In this post, we will explore the best practices for securing serverless applications, highlighting key considerations and steps that developers should take to ensure the safety of their serverless environments. We’ll cover areas such as identity and access management, encryption, vulnerability scanning, and best practices for securing the functions themselves.
Key Features of Serverless Security
- Event-Driven Execution: Functions are triggered by events, which must be securely managed to avoid malicious access.
- No Direct Server Access: Serverless abstracts infrastructure management, but you still need to secure the access points to your applications.
- Automatic Scaling: As serverless functions scale, ensuring secure scaling processes is critical.
- Data Protection: Secure storage and transmission of data in serverless applications are vital to prevent data breaches.
1. Implement Strong Identity and Access Management (IAM)
In serverless applications, Identity and Access Management (IAM) is a crucial layer of security. Properly managing permissions ensures that only authorized users and services can access or invoke your functions, preventing unauthorized access and ensuring that the principle of least privilege is applied.
Best Practices for IAM in Serverless
- Use IAM Roles and Policies: Assign minimal permissions to each Lambda function, API Gateway, or service to ensure they only have access to the resources they truly need.
- Follow the Principle of Least Privilege: Avoid assigning broad permissions (e.g., full access) to any function or user. Grant only the necessary permissions to reduce the attack surface.
- Use Temporary Credentials: When accessing AWS services, use temporary security credentials to avoid long-term credentials that could be compromised.
- Audit IAM Roles: Regularly audit and review IAM roles and permissions to ensure that access control remains appropriate as your serverless application evolves.
- Integrate with Federation Services: Use identity providers like OAuth or Active Directory to securely authenticate external users and integrate them into the system.
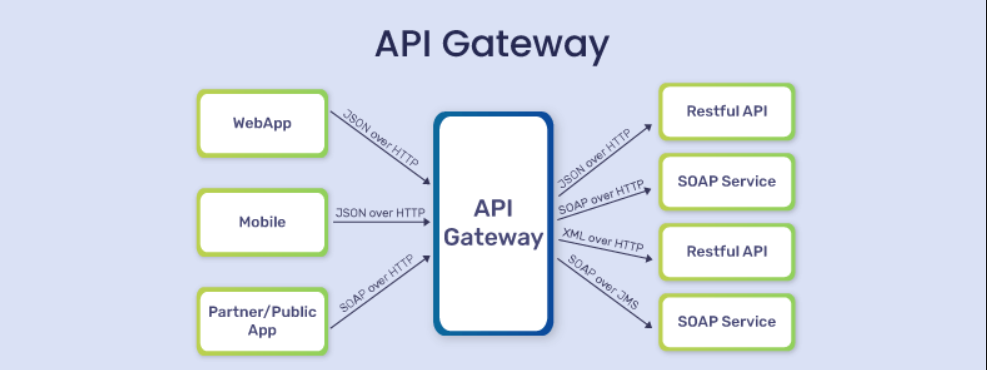
2. Secure API Gateway Endpoints
When exposing serverless functions via APIs, such as through AWS API Gateway or Azure API Management, securing the endpoints becomes critical. These endpoints are often the primary entry point for malicious actors, making them a common target for attacks like DDoS, injection, and data breaches.
Best Practices for Securing API Endpoints
- Use HTTPS for All API Requests: Always encrypt API traffic with HTTPS to ensure data is transmitted securely and cannot be intercepted by attackers.
- Enable Authentication: Use authentication methods like API Keys, OAuth, or AWS Cognito to ensure that only authorized users or applications can access your API endpoints.
- Rate Limiting: Implement rate limiting to mitigate DDoS attacks and prevent abusive usage of your APIs.
- Input Validation: Always validate and sanitize user inputs to prevent SQL injection or other injection attacks that might target vulnerabilities in the API.
- Use Web Application Firewalls (WAFs): Deploy WAFs in front of your API endpoints to block malicious requests and enhance overall security.
3. Encrypt Data in Transit and at Rest
Serverless applications often involve the transmission of sensitive data across networks and the storage of sensitive information in databases. Ensuring that data is encrypted both in transit and at rest is a fundamental security practice to protect it from unauthorized access.
Best Practices for Data Encryption
- Use TLS/SSL for Data in Transit: Ensure that all communication between serverless functions, APIs, and external services is encrypted using Transport Layer Security (TLS) or Secure Sockets Layer (SSL) to prevent eavesdropping and man-in-the-middle attacks.
- Encrypt Sensitive Data at Rest: Use encryption services like AWS KMS (Key Management Service) or Azure Key Vault to encrypt data stored in databases, S3 buckets, or other persistent storage locations.
- Use Environment Variables for Secrets: Store sensitive keys and credentials as environment variables within Lambda functions and use services like AWS Secrets Manager or Azure Key Vault to securely manage and access secrets.
- Encryption by Default: Enable server-side encryption for services like Amazon S3, RDS, and DynamoDB, ensuring that data is automatically encrypted as it is stored.
4. Vulnerability Scanning and Code Analysis
Despite the simplicity of deploying serverless functions, vulnerabilities in the code or misconfigurations in the cloud resources can still introduce security risks. Implementing regular vulnerability scanning and static code analysis ensures that potential security flaws are identified early in the development process.
Best Practices for Vulnerability Scanning
- Use Static Code Analysis Tools: Employ tools such as SonarQube or CodeQL to analyze your codebase for common vulnerabilities, security misconfigurations, and code quality issues.
- Scan Lambda Layers for Vulnerabilities: If using Lambda Layers, regularly scan for outdated or insecure libraries and dependencies that may introduce vulnerabilities.
- Use Third-Party Security Tools: Leverage services like Snyk or Dependabot to monitor for vulnerabilities in third-party packages or dependencies.
- Conduct Regular Penetration Testing: Run penetration tests on your serverless application to identify any exploitable vulnerabilities in the code or its integrations.
5. Monitor and Audit Serverless Applications
Continuous monitoring and auditing are essential for maintaining the security of serverless applications. Since serverless functions scale automatically and run in a stateless environment, it’s important to monitor function performance and logs to detect any anomalies or suspicious activities.
Best Practices for Monitoring and Auditing
- Enable CloudWatch Logs and Metrics: Use AWS CloudWatch or equivalent tools in other cloud providers to log function invocations, response times, errors, and other performance metrics. Monitoring these logs helps in quickly detecting suspicious activity or failures.
- Set Up Alerts for Anomalies: Configure CloudWatch Alarms or similar services to alert you in case of unusual behavior, such as unexpected spikes in traffic or high error rates in your serverless functions.
- Audit IAM Roles and Policies: Regularly audit IAM roles and policies for any changes that might expose your system to vulnerabilities or unauthorized access.
- Use AWS X-Ray for Tracing: AWS X-Ray helps trace and debug requests as they travel through various AWS services, providing visibility into the performance of serverless functions and assisting in identifying bottlenecks or security concerns.
6. Mitigating the Risks of Cold Starts and Function Timeout
Cold starts, where a function takes longer to initialize due to a lack of recent invocations, and function timeouts can both present security and performance risks. These issues can delay the response time of your serverless application, leading to a poor user experience and potential vulnerabilities if not properly managed.
Best Practices for Managing Cold Starts and Timeouts
- Optimize Lambda Function Initialization: Reduce the cold start time by minimizing dependencies and optimizing the code. Avoid using large packages and focus on keeping functions lightweight.
- Use Provisioned Concurrency: For critical functions that need to respond quickly, you can enable Provisioned Concurrency in AWS Lambda to reduce cold start latency by keeping a pre-warmed instance of the function running.
- Configure Appropriate Timeouts: Set function timeouts based on the expected execution time of your Lambda function. This prevents functions from running longer than necessary and reduces the risk of delayed responses.
- Monitor and Scale: Regularly monitor the execution times and cold start behaviors using CloudWatch and scale your functions appropriately to ensure consistent performance.
Building Secure Serverless Applications
Serverless computing offers significant advantages in terms of rapid development, automatic scaling, and cost efficiency. However, the inherent complexity and scalability of serverless systems also introduce security challenges. By following best practices for securing your serverless applications—such as implementing IAM policies, encrypting data, performing vulnerability scans, and setting up monitoring—you can minimize security risks and ensure the integrity and confidentiality of your applications.
As serverless technologies continue to evolve, keeping security at the forefront of development and deployment practices will be crucial to maintaining trust and ensuring the resilience of your cloud-native applications. By following these best practices and regularly reviewing your security posture, you can leverage serverless computing without compromising the security of your applications.