Here’s a comprehensive post titled “How to Secure Microservices: Authentication & Authorization Strategies” with expanded content for each section:
The Importance of Securing Microservices
In a microservices architecture, security is a crucial aspect of the overall design. Each microservice runs independently and communicates with others over a network, making it important to implement robust security measures to protect sensitive data and ensure the integrity of the entire system. Authentication and authorization are two of the core components of securing microservices, ensuring that only authorized users and services can access resources and perform certain actions.
In this post, we’ll explore the best practices for securing microservices through authentication and authorization strategies. By the end, you’ll understand how to design a secure microservices architecture and implement effective security controls.
Key Features of Authentication and Authorization
- Authentication: Verifying the identity of a user or service to ensure they are who they claim to be.
- Authorization: Determining whether a user or service has the appropriate permissions to access a specific resource or perform a particular action.
- Granular Access Control: Implementing policies that define which users or services can access which resources based on their roles or attributes.
- Centralized Management: Managing authentication and authorization centrally to ensure consistency and reduce complexity in microservices environments.
1. Authentication in Microservices: Verifying Identity
Authentication is the first line of defense when securing microservices. It ensures that users or services accessing the system are legitimate and have valid credentials. Without proper authentication, unauthorized access can compromise the entire system.
Authentication Strategies for Microservices
- JWT (JSON Web Tokens): JWT is a widely-used standard for securely transmitting information between services. It allows you to encode user identity and claims within a token that can be easily verified without requiring a central authority. The token can be signed with a secret key or an asymmetric key pair for added security.
- OAuth 2.0: OAuth 2.0 is a robust framework that provides secure, token-based authentication. It allows third-party applications to access user data without sharing user credentials. OAuth 2.0 uses access tokens to authorize service-to-service communication in microservices.
- API Gateway Authentication: In microservices architectures, the API Gateway can act as a single entry point for all incoming traffic. By integrating authentication protocols like JWT or OAuth, the API Gateway can verify requests before forwarding them to the appropriate microservices.
- Mutual TLS (mTLS): mTLS can be used to authenticate services by requiring both the client and server to present valid certificates during communication. This ensures that both parties are authenticated before any data is exchanged.
2. Authorization in Microservices: Defining Permissions
While authentication ensures that only legitimate users or services are allowed to interact with the system, authorization defines what they are allowed to do once authenticated. Authorization ensures that users or services can only access the resources and actions they are permitted to, preventing unauthorized actions.
Authorization Strategies for Microservices
- Role-Based Access Control (RBAC): RBAC is a widely-used approach where users are assigned roles (e.g., admin, user, guest), and each role has specific permissions to access certain resources or perform certain actions. This simplifies management by grouping permissions based on roles rather than individual users.
- Attribute-Based Access Control (ABAC): ABAC goes beyond roles and uses attributes (e.g., user location, resource type, or time of day) to determine access. This provides more granular control over who can access what based on contextual information.
- Scope-Based Authorization with OAuth: In OAuth 2.0, scopes define specific permissions that can be granted to an access token. For example, a service might have a scope to read data but not write it. This allows for fine-grained control over what each service or user is authorized to do.
- Policy-Based Access Control (PBAC): PBAC uses policies written in a language like XACML (Extensible Access Control Markup Language) to define complex rules and conditions for access. This method allows for dynamic and highly customizable authorization decisions based on various factors.
3. Securing Inter-Service Communication
In a microservices architecture, services often communicate with each other over a network. Securing these inter-service communications is essential to prevent unauthorized access, man-in-the-middle attacks, or data leakage.
Strategies for Securing Service-to-Service Communication
- Service Authentication with mTLS: As mentioned earlier, mTLS is an effective way to authenticate services during communication. It ensures that both parties in a communication channel are authenticated before exchanging sensitive data.
- API Gateway as a Security Layer: By using an API Gateway, you can centralize authentication and authorization checks, ensuring that every inter-service request is validated before being processed by a microservice. This can significantly reduce security risks.
- Token-Based Authentication: Services can use JWT tokens or other token-based systems to authenticate and authorize inter-service requests. Tokens should be signed and securely passed between services to verify that requests are legitimate.
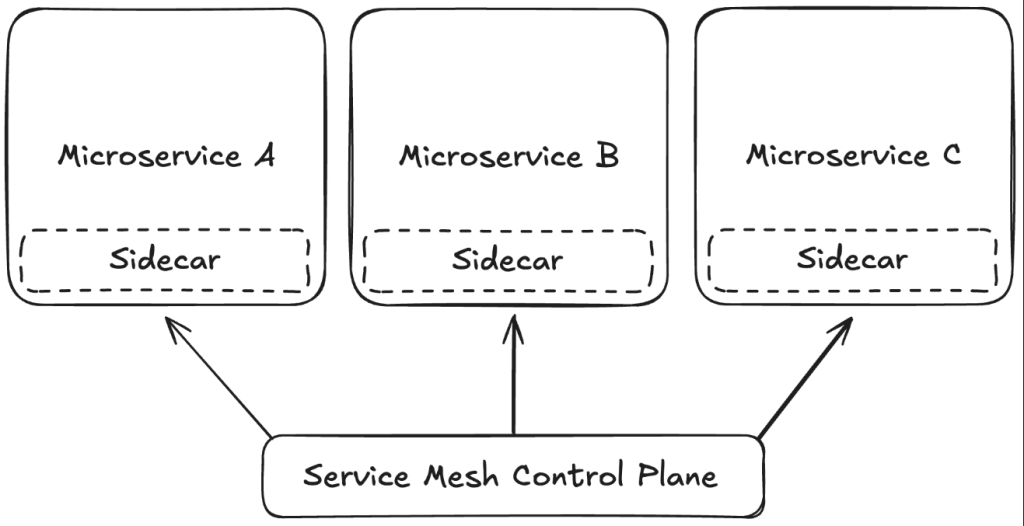
- Service Mesh: A service mesh like Istio or Linkerd can be used to manage the secure communication between services. These tools provide features like mTLS, service discovery, and traffic management, making it easier to secure microservices communication without modifying individual services.
4. Implementing Fine-Grained Access Control
Microservices often involve complex systems with various levels of access, meaning that fine-grained access control is essential to prevent unauthorized access to sensitive resources. Implementing this can be tricky, but it’s crucial for ensuring security in modern applications.
Best Practices for Fine-Grained Access Control
- Use Attribute-Based Policies: With ABAC, access control policies can be more dynamic and context-sensitive. For example, users might be allowed to access certain data only during specific hours or based on their geographic location.
- Scopes in OAuth 2.0: Use OAuth 2.0 scopes to define more granular access permissions. For example, a microservice might grant read access to one resource but restrict write access to another.
- Centralized Authorization Service: Consider implementing a centralized authorization service that manages and enforces policies across the entire microservices architecture. This ensures consistency in how access control is applied.
- Audit Logging: Keep detailed logs of all access requests and permissions changes to maintain an audit trail. This is useful for tracking security violations and ensuring compliance with regulatory requirements.
5. Monitoring and Auditing Security in Microservices
Continuous monitoring and auditing are essential components of a robust security strategy in microservices. These practices help identify security issues early and ensure compliance with security policies.
Best Practices for Monitoring and Auditing
- Centralized Logging: Use a centralized logging system like ELK Stack (Elasticsearch, Logstash, Kibana) or Prometheus for aggregating logs and monitoring metrics across all microservices. This allows for faster identification of security anomalies.
- Audit Trails: Maintain audit trails of authentication and authorization events, such as login attempts, token usage, and permission changes. This helps track potential unauthorized activities.
- Security Incident Detection: Implement security incident and event management (SIEM) tools like Splunk or Datadog to detect and respond to suspicious activities in real-time.
- Alerting: Set up automated alerts for events like unauthorized access attempts, service failures, or abnormal traffic patterns, which could indicate a security breach or vulnerability.
6. The Future of Microservices Security
As microservices architectures evolve, so too does the security landscape. The future of microservices security will likely focus on more advanced strategies to handle new challenges such as evolving threats, zero trust, and complex service-to-service communications.
Trends in Microservices Security
- Zero Trust Architecture: Zero Trust assumes that no one, whether inside or outside the network, can be trusted by default. Every request, even from within the system, must be authenticated and authorized. This approach is expected to become more widely adopted in microservices security.
- AI and Machine Learning: AI-driven security tools can help automate the detection of anomalies in traffic patterns, user behavior, or API requests. This will make it easier to identify potential vulnerabilities in real-time.
- Self-Healing Systems: Microservices are likely to become more self-healing, where security systems can automatically detect and respond to breaches, preventing them from spreading throughout the architecture.
- Advanced Service Meshes: Future service meshes will provide even more advanced features for securing inter-service communication, including fine-grained traffic management and stronger encryption techniques.
Protecting Microservices with Strong Authentication & Authorization
Securing microservices requires a multifaceted approach that combines effective authentication, authorization, and ongoing monitoring. By implementing strong authentication strategies like JWT and OAuth 2.0, enforcing fine-grained access control with RBAC or ABAC, and securing service-to-service communication through mTLS or API Gateways, you can ensure that your microservices architecture remains secure and resilient.
As your application grows and evolves, continuously monitor your system, audit access requests, and adopt advanced security strategies like Zero Trust and AI-driven detection to stay ahead of emerging threats. With these best practices in place, you’ll be able to protect your microservices architecture against vulnerabilities while maintaining the flexibility and scalability that microservices provide.
