Certainly! Here is an expanded version of the post “Challenges of Microservices and How to Overcome Them” with deeper insights into each section:
Understanding Microservices Challenges
The shift to microservices architecture has revolutionized how applications are built and maintained. Breaking down applications into smaller, independent services makes it easier to scale, develop, and deploy them. However, this flexibility and scalability come at a cost. Managing multiple services, handling data consistency, ensuring security, and orchestrating communications between services are just some of the challenges that organizations face as they adopt microservices.
Microservices allow for faster deployments, better fault tolerance, and the ability to scale individual services independently, but they also introduce complexity that must be addressed. In this post, we’ll examine the common challenges that arise with microservices and explore strategies to overcome them.
Key Features of Microservices Challenges
- Distributed System Complexity: The more services you have, the harder it becomes to manage communication, dependencies, and overall architecture.
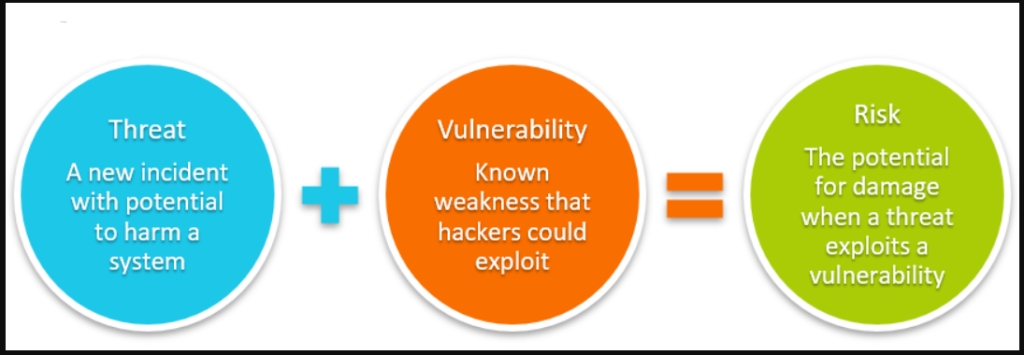
- Data Consistency: Ensuring data consistency across services with different databases is challenging, especially in distributed systems.
- Service Communication: Asynchronous and synchronous communication between services must be handled with care to avoid failures and inefficiencies.
- Operational Overhead: Microservices increase the number of components in the system, making infrastructure and operations more complex.
- Security: With multiple services communicating over networks, securing each service and the connections between them becomes a key challenge.
1. Managing Complexity in Microservices
As microservices architectures grow, managing the interactions and dependencies between a growing number of services becomes increasingly complex. Unlike monolithic applications, where all components are tightly integrated, microservices require each service to be independently deployable and manageable, introducing a new level of complexity.
How to Overcome the Complexity Challenge
- Service Discovery: Using service discovery tools like Consul, Eureka, or Zookeeper enables services to automatically discover and interact with each other, removing the need for hard-coded service addresses.
- API Gateway: Implementing an API Gateway simplifies communication between microservices by providing a unified interface to interact with different services. It can also manage cross-cutting concerns like load balancing, authentication, rate limiting, and logging.
- Centralized Logging and Monitoring: Implement centralized logging and monitoring tools such as ELK Stack, Prometheus, and Grafana. These tools aggregate logs and metrics across all services, giving developers and operators a single source of truth to monitor system health and performance.
- Containerization and Orchestration: Leverage Docker for containerization and Kubernetes for orchestrating the deployment and scaling of microservices. These tools help manage the complexity of deploying and scaling microservices across multiple environments.
- Use of Microservices Frameworks: Utilize frameworks designed to simplify microservices development and management, such as Spring Boot and Micronaut, which provide built-in support for service configuration, communication, and deployment.
Reducing complexity in microservices architecture requires the right set of tools and processes to ensure smooth service discovery, communication, monitoring, and scaling.
2. Handling Data Consistency and Integrity
One of the greatest challenges in microservices is managing data consistency across services. Unlike monolithic applications, which typically share a single database, microservices often have independent databases. This can create issues with maintaining data integrity and consistency, especially when services need to share data or remain synchronized.
Solutions for Managing Data Consistency
- Event Sourcing: In Event Sourcing, changes to data are stored as a series of immutable events rather than current state changes. This enables you to reconstruct the state of the system at any point in time, providing a solution for eventual consistency in distributed systems.
- CQRS (Command Query Responsibility Segregation): Implement CQRS to separate read and write operations. This allows for optimized handling of different data access patterns and can improve performance by allowing services to scale independently for different types of operations.
- Distributed Transactions: Use the Saga Pattern or Two-Phase Commit protocols to manage distributed transactions, ensuring that changes to multiple services are completed successfully or rolled back if any part of the process fails.
- Database Per Service: Each microservice should ideally manage its own database, which avoids tight coupling between services. However, you must ensure that eventual consistency is maintained, using techniques like eventual consistency or replication for data synchronization.
- Data Replication: Replicate data across services using a message broker or event-driven architecture (e.g., Apache Kafka), ensuring that all services have access to the most up-to-date information without direct database dependencies.
To manage data consistency in microservices, you must implement strategies that allow data to be synchronized across independent services while maintaining performance and scalability.
3. Service Communication and Interoperability
Microservices architecture is inherently decentralized, meaning that the services need to communicate with each other to provide end-user functionality. This communication, whether synchronous or asynchronous, must be managed carefully to avoid issues such as failures, delays, and inconsistent states.
Strategies for Efficient Service Communication
- Synchronous vs. Asynchronous Communication:
- Synchronous communication (e.g., REST, gRPC) is appropriate when services need immediate responses, such as querying data from another service.
- Asynchronous communication (e.g., message queues, Kafka, or event-driven architecture) is suitable for decoupling services and handling long-running processes, allowing services to process events or data at their own pace without waiting for responses.
- API Gateway: Use an API Gateway to centralize and manage communication between microservices. The API Gateway can handle request routing, load balancing, authentication, and authorization, allowing services to remain isolated while managing their interactions centrally.
- Service Mesh: A Service Mesh like Istio or Linkerd provides advanced capabilities for service-to-service communication, such as traffic management, load balancing, security (mTLS), and observability.
- Retry Logic and Circuit Breakers: Implement retry logic to automatically handle temporary communication failures. Use circuit breakers to prevent cascading failures in case of persistent issues with one service.
- Data Serialization Formats: Use efficient data serialization formats like Protocol Buffers (gRPC) or Avro to reduce the size and overhead of data being exchanged between services.
Ensuring effective communication between services requires a combination of the right protocols, tools, and fault tolerance mechanisms to avoid issues such as latency and downtime.
4. Operational Overhead and Maintenance
As the number of microservices in an application grows, so does the operational overhead. Managing deployments, monitoring, logging, and troubleshooting can become more complex as each microservice operates independently.
How to Minimize Operational Overhead
- Centralized Monitoring: Use tools like Prometheus, Grafana, and Datadog to monitor the health, performance, and resource usage of microservices in real-time. Centralized monitoring ensures that you can identify problems quickly, even when many services are involved.
- Container Orchestration with Kubernetes: Kubernetes is an essential tool for managing containerized microservices at scale. Kubernetes automates tasks such as scaling, failover, and deployment, reducing manual intervention and streamlining operations.
- Infrastructure as Code (IaC): Use IaC tools like Terraform, Ansible, or CloudFormation to automate the provisioning and management of infrastructure. IaC allows for consistent, repeatable, and scalable infrastructure management.
- CI/CD Automation: Set up CI/CD pipelines to automate testing, building, and deployment. Tools like Jenkins, GitLab CI, and CircleCI can be used to automate the delivery process, enabling fast, reliable releases.
- Microservices Management Platforms: Use platforms like Spring Cloud or Kubernetes for managing service discovery, configuration management, and service-to-service communication.
Minimizing operational overhead requires automation and centralized management to ensure that microservices are deployed, monitored, and scaled efficiently without manual intervention.
5. Security in Microservices
Microservices present unique security challenges because of the increased number of services and the communication between them. Each microservice needs to be individually secured, and communication between services must be encrypted to prevent unauthorized access.
Best Practices for Microservices Security
- Service-Level Authentication: Use OAuth 2.0 and JWT tokens to manage authentication and authorization between services. This ensures that each service can only access the resources it is authorized to use.
- API Gateway for Security: The API Gateway can act as the first line of defense, enforcing security policies such as authentication, authorization, rate limiting, and logging for incoming requests.
- Encryption of Data: Ensure that data is encrypted both at rest (e.g., using AES-256 encryption for databases) and in transit (using TLS/SSL for communication between services).
- Service-to-Service Communication Security: Use mTLS (mutual TLS) to authenticate and encrypt service-to-service communication, ensuring that only trusted services can communicate with one another.
- Access Control: Implement Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC) to define and enforce permissions for users and services, ensuring that only authorized entities can access critical resources.
Securing a microservices ecosystem requires consistent, layered security measures across services and communication channels to protect data and prevent unauthorized access.
Overcoming Microservices Challenges
Microservices offer numerous benefits, including flexibility, scalability, and faster development cycles, but they also introduce significant challenges. Managing the complexity of distributed services, ensuring data consistency, handling service communication, reducing operational overhead, and securing services are all critical hurdles that need to be addressed for a successful microservices implementation.
By adopting best practices like container orchestration, CI/CD automation, event-driven architecture, and robust security frameworks, organizations can overcome these challenges and reap the full benefits of microservices architecture. With careful planning, the right tools, and continuous monitoring, microservices can significantly improve the agility and resilience of software systems, enabling businesses to scale efficiently and deliver value to users faster.
