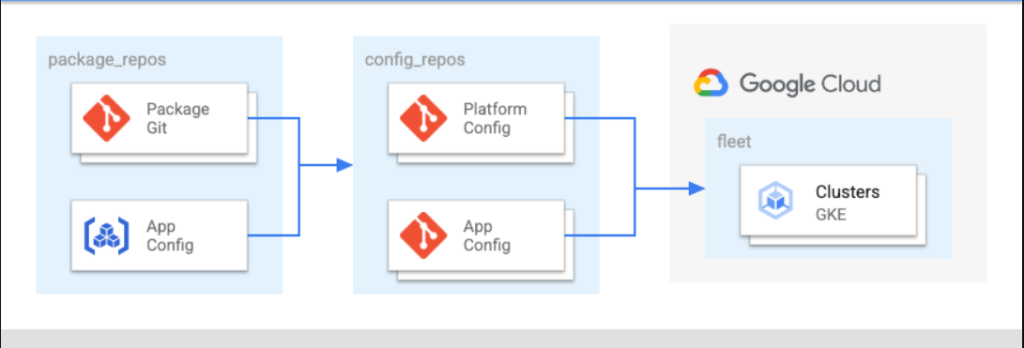
GitOps has transformed the way organizations deploy and manage applications and infrastructure in Kubernetes environments. With its automation and continuous deployment capabilities, GitOps simplifies the process of managing Kubernetes clusters using Git repositories as the single source of truth for configurations. However, this reliance on Git repositories introduces security concerns, as any vulnerabilities in the repository can have a significant impact on the integrity and security of both the infrastructure and the applications.
As GitOps becomes more widely adopted, securing the configuration management process is critical to ensuring the security of the entire pipeline. This post covers best practices for securing GitOps workflows, from securing Git repositories and Kubernetes clusters to managing secrets and implementing access controls. We’ll explore how to secure each layer of the GitOps pipeline, ensuring that teams can confidently leverage GitOps automation without compromising security.
1. What is GitOps Security?
GitOps security focuses on securing the workflow and infrastructure managed through GitOps, which automates application deployment and infrastructure management in Kubernetes environments. Since GitOps relies on Git repositories to define both application configurations and infrastructure setups, ensuring that these repositories, as well as the synchronization tools, are secure is paramount.
1.1 Key Components of GitOps Security
- Secure Git Repositories: The foundation of GitOps lies in Git repositories. Securing these repositories against unauthorized access and ensuring that their integrity is maintained is the first step in a secure GitOps pipeline.
- Continuous Monitoring and Auditing: GitOps tools continuously monitor repositories for changes and synchronize them with Kubernetes clusters. This monitoring must be secure and provide audit trails to track any unauthorized or accidental changes.
- Access Control: Both Git repositories and Kubernetes clusters require stringent access controls to ensure that only authorized users and services can modify or deploy configurations.
By integrating these security best practices, teams can reduce the risk of malicious activity or configuration drift and ensure that their GitOps workflows are protected from external threats.
2. Best Practices for Secure GitOps Configuration Management
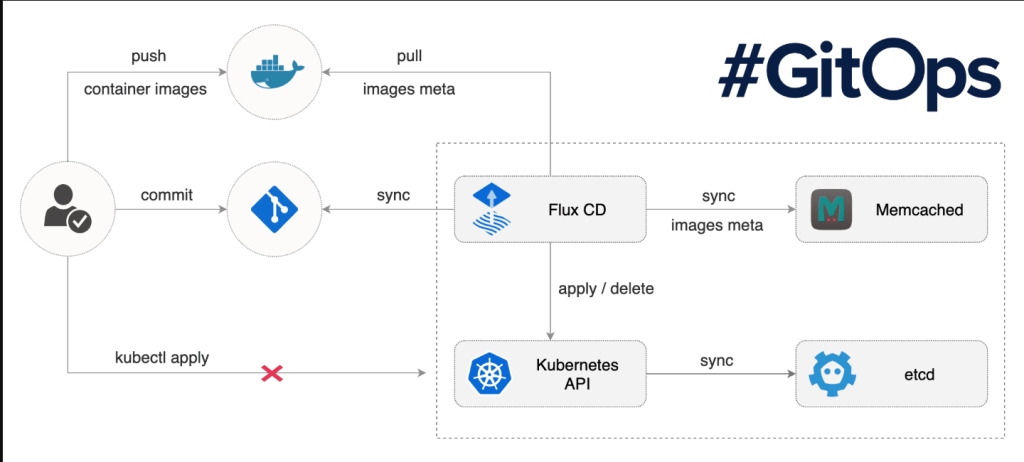
To ensure that GitOps configurations are securely managed, teams must implement proper controls over the Git repositories, Kubernetes clusters, and all associated workflows. Below are key practices to follow:
2.1 Use Private Git Repositories
- Keep Configurations Secure: Store all configuration files, including Kubernetes manifests, application configurations, and infrastructure settings, in private Git repositories to prevent unauthorized access.
- Protect with Strong Authentication: Use strong authentication methods such as SSH keys or personal access tokens (PATs) for repository access. Avoid using basic authentication or passwords.
- Encrypt Sensitive Data: Never store sensitive information, such as passwords or API keys, in plaintext within Git repositories. Use secrets management tools to inject secrets into your Kubernetes clusters at runtime.
By using private repositories and strong authentication mechanisms, teams can significantly reduce the risk of external access to sensitive GitOps configurations.
2.2 Git Commit and Branch Protection
- Enforce Branch Protection Rules: Protect critical branches (like
mainormaster) in your Git repositories by enforcing rules that prevent direct pushing. Use pull request-based workflows for all changes to ensure that changes are reviewed before being applied. - Require Signed Commits: Use commit signing (GPG keys) to ensure that commits are verified and come from trusted contributors. This helps prevent malicious actors from making unauthorized changes to your Git repositories.
- Enforce Code Reviews and Approvals: Set up mandatory code reviews for all changes to infrastructure or application configurations. Ensure that every change is approved by authorized reviewers before being merged.
These measures ensure that only authorized and reviewed changes are made to the Git repositories, maintaining the integrity of the configurations.
2.3 Granular Access Control for Git Repositories
- Role-Based Access Control (RBAC): Implement RBAC to ensure that only those who need access to the repository have it. For instance, developers can have access to modify application code, while operations teams may have access to infrastructure-related configurations.
- Limit Access to Secrets: Restrict access to sensitive data by using secrets management tools. For example, secrets such as database credentials should be injected securely into Kubernetes clusters at runtime and not stored in the Git repository.
- Audit and Logging: Enable logging for all actions performed on your Git repositories. Ensure that these logs are retained and accessible for security audits, tracking who made changes and when.
By implementing granular access control policies, organizations can ensure that only authorized individuals or services have access to specific resources and configurations.
3. Kubernetes Cluster Security in GitOps
In a GitOps pipeline, Kubernetes clusters serve as the execution environment where configuration changes are deployed. Securing Kubernetes clusters is just as important as securing Git repositories, as any vulnerabilities in the cluster can result in unauthorized deployments, data leaks, or potential outages.
3.1 Use Kubernetes RBAC for Fine-Grained Permissions
- Define Least Privilege Roles: Kubernetes RBAC (Role-Based Access Control) enables teams to define permissions at a granular level. Ensure that users and service accounts are granted only the permissions they need to operate, following the principle of least privilege.
- Service Accounts for Automation: When using GitOps tools like ArgoCD or FluxCD, ensure that the service accounts used by these tools have only the necessary permissions for syncing changes from Git repositories to Kubernetes clusters.
- Review and Audit Roles Regularly: Kubernetes roles should be regularly reviewed and audited to ensure that they are still aligned with the current needs of the team. Role changes should also be tracked in Git to maintain an audit trail.
By implementing RBAC for all users and service accounts, you can ensure that Kubernetes clusters are protected from unauthorized access and that privileges are only granted to users who need them.
3.2 Network Policies and Isolation
- Control Pod-to-Pod Communication: Use Kubernetes network policies to restrict communication between pods, ensuring that only authorized pods can communicate with each other. This helps to prevent lateral movement in the event of a compromise.
- Segment Clusters: For larger organizations or multi-tenant environments, segment Kubernetes clusters into separate namespaces and implement strict network isolation between them. This limits the impact of a breach in one namespace on others.
Network policies and isolation reduce the attack surface within Kubernetes clusters and help ensure that workloads are properly secured.
4. Auditing, Monitoring, and Logging Changes in GitOps
Effective auditing, monitoring, and logging are essential for detecting and responding to security incidents in GitOps workflows. Since GitOps tools automatically apply changes to Kubernetes clusters, it’s vital to continuously monitor both the Git repository and the Kubernetes clusters for any unauthorized activities.
4.1 Git Repository Auditing and Logging
- Track Repository Changes: Git repositories should be monitored for changes, especially for critical configuration files. Use tools like GitHub Actions, GitLab CI, or other Git auditing tools to detect suspicious activity or unauthorized changes.
- Integrate with SIEM Systems: Security Information and Event Management (SIEM) systems can be used to aggregate logs from Git repositories, Kubernetes clusters, and GitOps tools. This enables real-time alerts for suspicious activities and unauthorized changes.
Auditing and logging in Git repositories provide visibility into all changes made to the configurations, helping teams track who made changes and identify any unauthorized actions.
4.2 Monitor Kubernetes Clusters for Anomalies
- Enable Kubernetes Audit Logs: Kubernetes audit logs track all interactions with the Kubernetes API, providing valuable insights into who is making changes to the cluster and when. These logs should be enabled and stored in a centralized location.
- Monitor Cluster Metrics: Use monitoring tools like Prometheus and Grafana to collect real-time metrics from your Kubernetes clusters. Set up alerts for abnormal behavior, such as unusual deployment activity or configuration changes.
- Use Automated Remediation Tools: In the event of a detected anomaly, use automated remediation tools to rollback to a known good state or fix misconfigurations. This minimizes the impact of a potential security breach.
By continuously monitoring Kubernetes clusters, organizations can quickly detect and respond to unauthorized activities, ensuring the security of the entire pipeline.
5. Secrets Management in GitOps
GitOps workflows often involve deploying configurations that require sensitive information, such as API keys, credentials, or tokens. Storing secrets securely is one of the most critical aspects of securing a GitOps pipeline.
5.1 Never Store Secrets in Git Repositories
- Use External Secrets Management: Use tools like HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault to manage and store secrets securely. These tools provide encryption and access controls to protect sensitive information.
- Secrets Injection at Runtime: Instead of storing secrets in Git repositories, inject them into Kubernetes clusters at runtime using Kubernetes Secrets or tools like Helm Secrets or Sealed Secrets. This ensures that secrets are only available to authorized applications at runtime.
- Use Environment Variables for Secrets: When passing secrets to applications, use environment variables or configuration files that are encrypted and not hardcoded into Git repositories.
By using external secrets management solutions and injecting secrets securely into Kubernetes clusters, organizations can protect sensitive data and prevent exposure through Git repositories.
5.2 Automate Secret Rotation and Auditing
- Automated Secret Rotation: Secrets should be rotated periodically to minimize the risk of leakage or unauthorized access. Many secrets management tools support automatic secret rotation.
- Audit Access to Secrets: Monitor and audit access to secrets to ensure that only authorized users and services are accessing them. Most secrets management tools provide logging and auditing features to track secret usage.
Automating secret rotation and auditing secret access enhances the security of the GitOps workflow, ensuring that secrets are kept secure and access is properly managed.
6. The Future of GitOps Security
As GitOps continues to gain traction, the security landscape surrounding it will evolve. The integration of machine learning, AI, and advanced security automation will play a significant role in the future of GitOps security.
6.1 AI and Machine Learning for Proactive Security
- Predictive Threat Detection: AI can analyze patterns in GitOps workflows to predict potential security risks or breaches before they occur. This proactive approach can reduce the time it takes to detect and respond to security incidents.
- Automated Security Remediation: Machine learning-powered tools could automatically detect vulnerabilities in Kubernetes clusters or configuration files and apply fixes or alerts, reducing manual intervention.
The future of GitOps security lies in using AI and machine learning to predict and prevent security issues before they become critical.
6.2 Enhanced Compliance Automation
- Automated Compliance Audits: As organizations face increasing regulatory pressure, GitOps tools will continue to evolve to include automated compliance checks. These tools will automatically ensure that configurations meet regulatory standards like GDPR or HIPAA.
- Security as Code: With security as code becoming more common, GitOps workflows will integrate more deeply with automated compliance tools to ensure security policies are enforced at every stage of the deployment pipeline.
With compliance automation and security as code, GitOps will continue to offer both agility and security, making it easier for organizations to meet regulatory requirements.
